It can feel like every day there’s news of another massive data breach. From Marriott’s security incident of over 5 million unencrypted passport numbers being stolen to Under Armour’s MyFitnessPal hack of 150 million users, consumers are increasingly wary about how their data is being handled by corporations. The increasing size and frequency of headline-worthy breaches are also bringing with it the potential for real impacts to revenue and enterprise valuation, not to mention reputational damage, FBI investigations, and congressional hearings.
Breaches are not random, nor anecdotal. Instead, the likelihood of a data breach involving a minimum of 10,000 records is now estimated at approximately 27.9 percent over a 24-month period. When a breach occurs, many questions are asked, ranging from how did this happen to what did we lose and what is our liability?
All are important questions. But ironically, many of the answers to the questions point back to a basic Information Governance problem, starting with the lack of meaningful insight into the contents of their global data universe – particularly their vast stores of unstructured data.
Analysts at Garter estimate that approximately 80% of the world’s data is unstructured, which comes in the form of emails, social media, blogs, documents, images and videos. Companies love to collect data – whether it’s of use to them or not. There is a myth that “all data is good data” which is fundamentally untrue. The more data you have lying around, the greater the risk to your organization.
We hear from companies all the time “I have too much data. I don’t know where it is. I don’t know how to protect it.” Hackers are always looking for the weakest/easiest path to steal sensitive data – and unstructured data provides that entry point. With unstructured “dark” data containing unknown levels of risk, it can no longer be ignored by CISOs or CTOs.
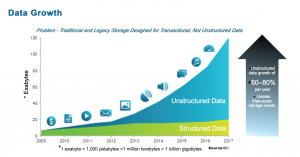
Companies collecting and storing sensitive information need to build processes and procedures to limit the potential fallout from a data breach. In order to confront information risk in unstructured content it’s best to start by following some of these basic steps:
- Map your data estate to identify different types of unstructured data
- Identify why unstructured data exists by discussing ownership and codification processes
- Address stale data stores by disposing of ROT (Redundant, Obsolete, Trivial) data
- Use legislation, litigation and regulation requirements as business drivers
- Leverage file analytics tools to contextualize and quantify information risk
- Take a holistic approach to information governance and put controls in place moving forward
The Bottom Line
As the number and magnitude of data breaches continue to increase, organizations must deal with the information risk in their unstructured content in order to minimize potential breach damage. The unstructured data problem can no longer be swept under the carpet – the impact of a data breach is too big to ignore. Data governance solutions, such as Active Navigation’s Discovery Center, can help enterprise organizations mitigate their risk in unstructured data.
Contact us to schedule a demo and find out what’s hiding in your unstructured data.
